Nakisa Security: Your data in the best hands
- Data encryption in rest and in transit
- SOC 1 Type II & SOC 2 Type II audit reports
- GDPR requirements
- Role-based permissions
- Single sign-on (SSO)
What is Nakisa
Our solutions include:
– Nakisa Lease Administration: a solution for lessees and lessors to have full control over growing portfolios of leased assets and ensure compliance with IFRS 16, ASC 842, and GASB 87.
– Nakisa Real Estate: a solution for commercial real estate teams for day-to-day operations, real estate portfolio management and optimization, and accounting compliance.
– Nakisa HR Suite: a solution for HR professionals to manage workforce planning, organizational design, visualization, and analytics, as well enabling them to predict the effect of a future event on human capital.
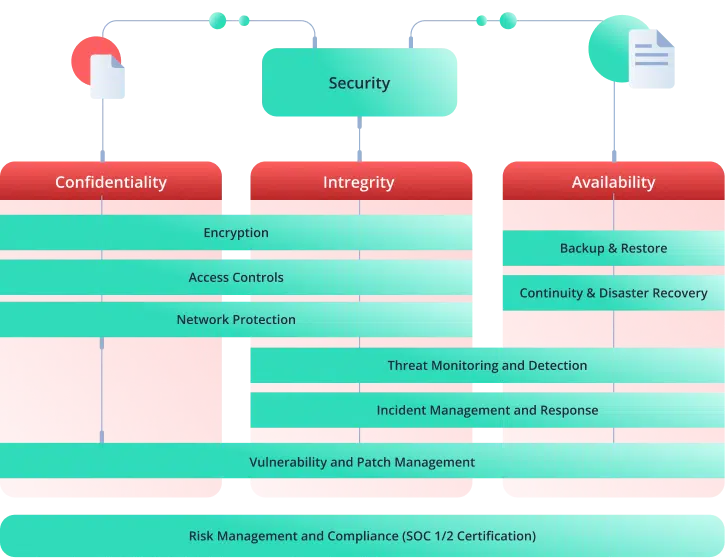
Your Security is Our Priority
Building trust means peace of mind. That’s why we promise our clients we’ll be their most trusted software partners—and we deliver on that. Nakisa uses the most established, industry-proven cybersecurity and risk management practices and resort to the leading technology services providers.
Also, our experts rigorously follow the latest industry standards to protect your data and systems at every stage of their lifecycles. This way, you can perform your daily operations and design your business strategy with all tranquility.
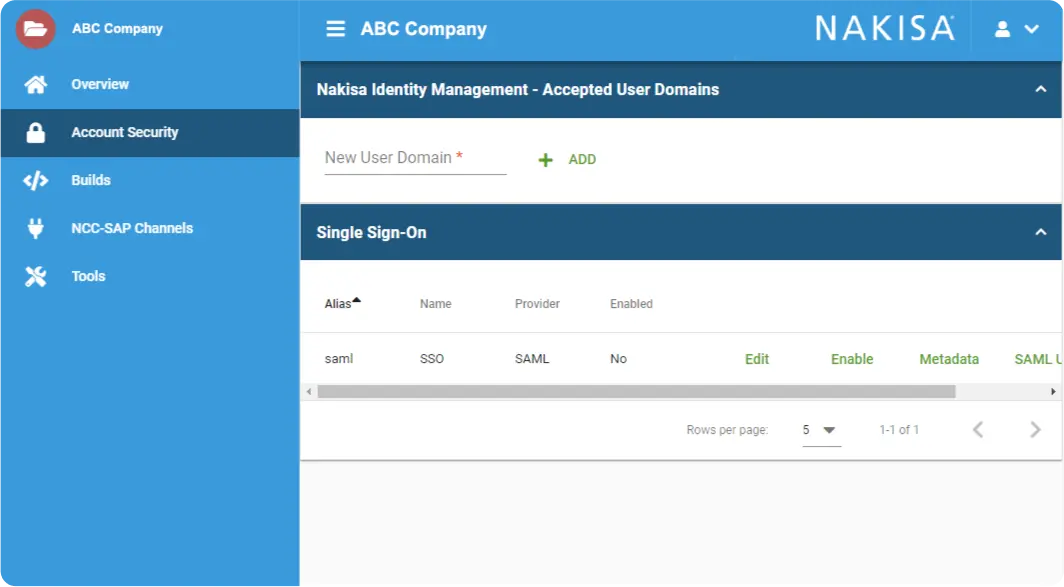
Welcome to our Security Cockpit
- Manage identities and access with out-of-the-box role-based access controls
- Run authentication mechanisms, including single sign-on (SSO) and multi-factor authentication.
- Monitor the state of their solutions and environments, ensuring everything runs smoothly for users.
Certifications & audits
As the security and privacy of your data is our priority, we take every step necessary to assure our clients of this commitment. This includes voluntarily undergoing the lengthy process of independent third-party certification based on industry standards.
As part of Nakisa SOC 1 Type II & SOC 2 Type II audit report, which is released on an annual basis by a global 3rd party auditing firm, Nakisa has implemented and adheres to strict information protocols, including the security, availability, processing integrity, confidentiality, and privacy of our partners’ data.
The above SOC reports, penetration test reports, and other certifications are available in December of each year to our partners and prospects upon request. To request any of our certifications or reports, click here.
GDPR requirements
- Search for records within the app, with support to remove specific information if needed.
- Providing our clients with configurable privacy and compliance settings such as using their own SSO, controlling who can access the application and what kind of information, and more.
- Providing sufficient data transfer methods to our clients.
- Maintaining records of processing activities.
- Training employees on security and privacy practices.
Our third-party security measures
Nakisa’s data center providers employ a variety of security mechanisms, covering both physical and virtual access. Our data center providers are all certified by independent auditors and third-party organizations so that we can deliver the best security measures available to our global clients.
Nakisa’s service providers comply with the following standards:
C5 [Germany]
Cyber Essentials Plus [UK]
DoD SRG, FedRAMP, FIPS IRAP [Australia]
ISO 9001, ISO 27001, ISO 27017, ISO 27018
MLPS Level 3 [China]
MTCS [Singapore]
PCI DSS Level 1, SEC Rule 17-a-4(f), SOC 1/2/3.
Encryption of data at rest and in transit
Encryption key management
User authentications and profiles
Single sign-on support
Nakisa Identity and Access Management (NIAM)
How do Nakisa engineers access the systems to provide support?
Under Nakisa’s Access Management policy, when an issue is raised via our support ticketing system, our support team will request client approval for temporary access to investigate and resolve the issue for the specific environment/s. This access is granted for a limited time, enough to resolve the ticket with auto closure enabled by the system when access is approved.
In addition to our annual third-party SOC audit, and as part of Nakisa’s Access Management policy, internal audits are performed regularly:
- High privileged and user accounts review is performed at least twice a year.
- Logs are reviewed monthly.
- Monitoring tools are in place with notification to appropriate individuals for abnormal events/activities.
- Access authorizations and requests are reviewed periodically.
Cloud infrastructure access and authorization
For greater security while accessing our cloud infrastructure, Nakisa has an Access Control List (ACL) that ensures only pre-approved cloud engineers can perform specific tasks defined by their roles. To access the cloud infrastructure, we utilize multi-factor authentication (MFA), which requires approval from different managers and heads of departments, with the final required approval from our Chief Security Officer.
In addition to our annual third-party SOC audit, and as part of Nakisa’s Access Management policy, internal audits are performed regularly to review such accesses and corresponding logs.
Application logs & auditing
Application logs enable you and your auditors to review all the activities performed by the users and the system to ensure data integrity. We allow our clients and their auditors to leverage our ITGC capabilities and log all types of activities and data transfers in the system.
You can easily review and download all the logs, which demonstrate all types of activities by the users, such as system access, data, and configuration modifications, as well as system activities, such as automatic jobs and other data communications between Nakisa solutions and any other solutions integrated, directly from the Nakisa applications. You can also revert actions when needed.
Dedicated, encrypted site-to-site integration through Nakisa Cloud Connector (NCC)
Secure Software Development Life Cycle (SSDLC)
Security is at the core of our software design. We’ve adopted numerous best practices and leverage the OWASP framework for our software development to ensure security by design right from the start.
Code Review
All changes to our code are tested by our Quality Assurance (QA) team, and criteria are established for performing code reviews, web vulnerability assessments, and advanced security tests. We conduct manual and automated code reviews before checking in code. After code checks, the QA teams perform regression and functionality tests. In addition, we also use in-house and third-party solutions such as Veracode to conduct vulnerability assessments and security tests on our application. Vulnerability tests are carried out before each release, and as often as needed, where we test the solution from A to Z. Upon development, we deploy in a lower environment to enable stakeholders to test the solution before deployment in the production system. All such activities are recorded as part of our change management policy (please note that our auditors validate our enforcement of changes as part of SOC 2 audits).
Quality assurance
Each product release is put through a stringent functionality test, performance tests, stability tests, and UX tests before they are released. We validate the releases in internal builds followed by lower environments before pushing them to the production system following our change management policy.
Vulnerability assessment & penetration testing
We use various tools for analyzing the code and checking for security vulnerabilities, such as Veracode and OWASP, before any release. Our strategy is to prevent security vulnerabilities first, then use industry-standard validation tools and techniques to validate that prevention worked. Issues identified through vulnerability assessments, penetration tests, and network vulnerability scanning are prioritized based on criticality and risk.
Vulnerability scans, including SAST (Static Application Security Testing), DAST (Dynamic Application Security Testing), Container and Dependency Scanning, and Penetration Testing, are carried out in every release and as often as needed. Following the best practices of OWASP, we aim to identify and remove standard and advanced web application security vulnerabilities, including, but not limited to, the following:
- Cross-site request forgery (CSRF)
- Cross-site scripting (XSS)
- Improper input handling (SQL injection, XML injection…)
- HTTP response splitting
- Authentication and authorizations
We leverage a global 3rd party auditing firm to perform penetration testing on our solution, and the report on such tests can be provided to you upon request. We also offer all our SaaS clients the ability to conduct penetration testing on the lower environment of the solution, enabling you to evaluate Nakisa’s cloud security and measures yourselves. In order to perform a penetration test, please discuss your penetration testing needs with your Nakisa Client Success Manager.
Malware protection
Nakisa Cloud only uses non-Windows operating systems, and all systems follow a hardening baseline policy for security management. Note that our deployment architecture is based on DMZ, and no end-user access is available to server resources at the OS level. User-uploaded documents are not stored in the server file system and are not accessed at the server level. Also, Intrusion Detection Systems and Intrusion Protection Systems (IDS/IPS) and firewall layers secure inbound and outbound access on system ports, monitoring and reporting login attempts, account creations, and periods of system non-availability. All Nakisa employees use systems that have antimalware, supporting real-time scanning and security, and automatic updates are enabled on devices.
Security Monitoring
We have various security measures and systems that continuously monitor for malicious activity, attacks, and unauthorized behavior from multiple perspectives. Our team can mitigate any potential attacks by following the internal procedure set for such events. We share our security systems, architectures, and test results with our SOC 2 auditing firm, and you can review such measures upon requesting the SOC report.
Business continuity, disaster recovery, and backups
Nakisa’s disaster recovery plan provides that in the event of a disaster defined as a natural or human-made condition that could render your subscription services inaccessible for more than one day (“Disaster”), Nakisa can resume services following this Subscription Services Agreement within one day from the event. RTO (Recovery Time Objective) for Nakisa cloud solutions is within one day, and RPO (Recovery Point Objective) is the last daily backup.
As part of Nakisa’s compliance process and SOC auditing, disaster recovery capabilities and plans are tested continuously. Disaster recovery simulation events are conducted by creating an event that results in losing an imaginary client’s data and access to their system. This test requires Nakisa to declare a disaster and trigger our DR action plan, as our Support & Cloud Services teams cannot bring the system back up. A data restore is triggered on a newly built infrastructure and restores the latest backup within our contractual timeframe.

Disaster recovery on the cloud is done by leveraging our cloud service provider’s resource availability on-demand. Using our cloud service provider’s specific APIs, a failed resource is restarted automatically in the case of a crash, and a backup is used to restore the system. Restoration and disaster recovery are achieved using the most recent or desired backup file and restoring all backed-up data.
Concerning our client’s production environment, Nakisa shall provide the following data back recovery points.
- Client data backups are stored in the same region as the client instance but in different data center locations to ensure recoverability in the event of a natural disaster.
- The backups will be periodically tested as part of the BCP (Business Continuity Planning) testing.
- The backup logs will be reviewed for errors and abnormal durations, and we look for opportunities to improve backup performance.
- Corrective actions will be taken when backup problems are identified to reduce risks associated with failed backups.
Note that a calendar week starts on Sunday at 12:00 AM until the following Saturday at 11:59 AM ET.
Backup Types
Daily
Weekly
Monthly
Available Recovery Points
Any of the last 7 daily backups
Any of the last 4 weekly backups
Any of the last 3 monthly backups
Data sovereignty & transparency
Incident management
Nakisa Service Level Agreement (SLA) for security incidents and mitigations
In case of any potential or active security incident of which Nakisa is made aware, we address the security ticket following a priority level assessment – low, medium, high, or critical – based on the security incident’s impact on our clients. We provide different mitigation timelines in addition to daily updates and root cause analysis documentation that captures the required details and indicates the preventative actions that will be taken in the future.
Physical perimeter security
Datacenter physical security begins at the Perimeter Layer. This layer includes several security features, including, but not limited to, 24/7 security guards, fencing, surveillance cameras, and intrusion detection technology. This includes scrutiny of the access, controlling the entry, monitoring for unauthorized entry, etc. All physical access to the inside perimeter layers is highly restricted and stringently regulated, and logs are available for periodic review.
Capacity management & load balancing
We leverage a global third-party provider’s services to offer on-demand and automatic capacity expansion and distribute traffic from our clients across multiple zones to support high availability. While ensuring no one server is overworked, which could result in degraded performance or unavailability (See “Availability” section for more details), you can instantly expand or reduce the capacity needed without technical support or additional investment in the infrastructure.
Cloud availability
We provide up-time of at least 99.5% for our Cloud (SaaS) clients with high availability. Using the latest cloud technologies enables us to increase resources on the run and ensure continuous system operations if systems face issues. This means our clients do not have to deal with poor system performance or major downtime.
Monitoring
We have various security measures and systems that continuously monitor for malicious activity, attacks, and unauthorized behavior from multiple perspectives. Our team can mitigate any potential attacks by following the internal procedure set for such events. We share our security systems, architectures, and test results with our SOC 2 auditing firm, and you can review such measures upon requesting the SOC report.
System and performance monitoring
We have various security measures and systems that continuously monitor for malicious activity, attacks, and unauthorized behavior from multiple perspectives. Our team can mitigate any potential attacks by following the internal procedure set for such events. We share our security systems, architectures, and test results with our SOC 2 auditing firm, and you can review such measures upon requesting the SOC report.
Maintenance
All scheduled and planned updates to Nakisa applications during which Subscription Services may not be available to our clients take place during our standard maintenance window over the weekend to minimize user disruption. The client will be notified of any other planned downtime seventy-two hours in advance. Nakisa will diligently mitigate the risk of undue disruption to normal business operations. In case of emergency maintenance where Nakisa needs to make the Subscription Services unavailable to perform a maintenance operation outside of any Scheduled Downtime period, the clients will be notified of an Emergency Maintenance as soon as possible.
Nakisa SLA for support
While our configuration management process and proactive monitoring prevent most issues from affecting you, we’re prepared to respond when an event causes downtime of your system. We’re pleased to solve any issues based on our industry-standard response times. However, we understand that some issues require immediate attention. Thanks to our escalation policy, you can rest assured that the necessary resources will be allocated for a timely resolution when needed. We also perform regular tests of our disaster recovery capabilities to ensure we’re ready to respond efficiently and promptly when unplanned downtime happens.
Frequently asked questions
- Change Management Policy;
- Risk Management Methodology;
- Access Management Policy;
- Information Security Policy;
- Risk Management policy;
- Information Asset Management Policy;
- Incident Management Policy;
- Data Retention and Disposal Policy;
- Data Protection Policy;
- Data Retention and Disposal;
- Information Security Awareness Policy.
Nakisa’s approach to security is built on the shared responsibility model with leading and trusted cloud service providers. While we regularly review the third-party audit reports of our cloud service providers, internally, we share the responsibility of security controls throughout the organization, including HR, IT, CloudOPS, Products, and R&D. We leverage frameworks such as NIST CSF (National Institute of Standards and Technology Cybersecurity Framework) and CSA CCM (Cloud Security Alliance Cloud Controls Matrix) and attest to our system’s description and controls through our SOC Type 1 and SOC Type 2 reports.
All client data is isolated, segregated, and encrypted using unique key encryption for each client.
Nakisa’s environments are not publicly accessible and can only be accessed via a Virtual Private Cloud (VPC). Additional protection is provided by ACL (access control list) firewall rules that only allow traffic from specified ports to and/or from specific destinations. Access is exclusively via HTTPS and uses a reverse proxy to protect the environment from the outside world.
Data is encrypted in transit using standard secure web protocols and at rest using cloud service providers’ volume encryptions. Our cloud service providers administer the encryption method and key management infrastructure.
Nakisa works with trusted cloud service providers to constantly monitor the environment’s security, and we’ll take necessary corrective action to mitigate the risk of intrusions. We leverage monitoring and detection tools to identify potential threats and follow our incident management processes to triage alerts and take the necessary actions.
We follow a diligent change management policy with procedures for the segregation of duties. Security is a significant component that could drive a change in our solutions to ensure that risks are treated following their evaluation. Security also evaluates changes and is a stakeholder in the change management process.
The high-availability, scalable, elastic environment enabled by our cloud service providers offers automated, online, encrypted backup functionality to ensure that all data is redundantly stored and secured.
As per the Nakisa Incident Management policy, a support case is triggered after each security incident, whether identified through our monitoring and detection tools or by a user. This support case details the incident and flags the appropriate level of urgency. Resources are assigned as needed to each incident based on support triage.
If you’re an existing client, please contact your Account Manager for more details.
Considering Nakisa solutions? Reach out to our team today to get all your security questions answered! If you are an existing client, please contact your Account Manager for more details.